Subnetting in Practice
Subnetting works by applying the concept of extended network addresses to individual computer (and other network device) addresses.
An extended network address includes both a network address and additional bits that represent the subnet number... (see below)
.. . Together, these two data elements support a two-level addressing scheme recognized by standard implementations of IP. The network address and subnet number, when combined with the host address, therefore support a three-level scheme.
Consider the following real-world example. A small business plans to use the 192.168.1.0 network for its internal (intranet) hosts. The human resources department wants their computers to be on a restricted part of this network because they store payroll information and other sensitive employee data. But because this is a Class C network, the default subnet mask of 255.255.255.0 allows all computers on the network to be peers (to send messages directly to each other) by default.
The first four bits of 192.168.1.0 -
1100
place this network in the Class C range and also fix the length of the network address at 24 bits. To subnet this network, more than 24 bits must be set to '1' on the left side of the subnet mask. For instance, the 25-bit mask 255.255.255.128 creates a two-subnet network as follows.
For every additional bit set to '1' in the mask, another bit becomes available in the subnet number to index additional subnets. A two-bit subnet number can support up to four subnets, a three-bit number supports up to eight subnets, and so on.
Private Networks and Subnets
As mentioned earlier in this tutorial, the governing bodies that administer Internet Protocol have reserved certain networks for internal uses. In general, intranets utilizing these networks gain more control over managing their IP configuration and Internet access. The default subnet masks associated with these private networks are listed below.
Consult RFC 1918 for more details about these special networks.
Subnetting Review
Subnetting allows network administrators some flexibility in defining relationships among network hosts. Hosts on different subnets can only "talk" to each other through specialized network gateway devices like routers. The ability to filter traffic between subnets can make more bandwidth available to applications and can limit access in desirable ways.
source :http://compnetworking.about.com
Rabu, 04 Maret 2009
IP Tutorial Subnet Masks and Subnetting
Label: NetworkingInternet Protocol Summary - Facts about IP
By Bradley Mitchell, About.com
Name: Internet Protocol - abbreviated "IP"
Description: IP is used by many higher level network protocols, principally TCP and UDP. Many Internet software applications including Web browsers, FTP clients, and email programs, rely on Internet Protocol.
OSI Model: Network layer (Layer 3)
Datagram Format: A base header 20 bytes (5 "longwords") in length, with the option for expanded header options, followed by data.
Header:
Word 1 -
• Version - 4 bits
• Header Length (in longwords) - 4 bits
• Type of Service / Differentiated Services Code Point (DSCP) - 8 bits
• Datagram Length (in bytes) - 16 bits
Word 2 -
• ID Number - 16 bits
• Fragmentation Flags - 3 bits
• Fragmentation Offset - 13 bits
Word 3 -
• Time to Live - 8 bits
• Transport Protocol - 8 bits
• Header Checksum - 16 bits
Word 4 -
• Source IP Address - 32 bits
Word 5 -
• Destination IP Address - 32 bits
Variable length fields -
• Options
• Padding
Payload: IP datagram payloads can be of variable length. The minimum size of an IP datagram is 28 bytes, using the minimum 20 bytes of header information, followed by the minimum of 8 bytes of data. The maximum size of an IP datagram payload is 65,535 bytes minus the header size.
Footer: Internet Protocol does not use its own datagram footer.
source :http://compnetworking.about.com
Internet Protocol Tutorial IP Loopback, IP Private Addresses, and IPv6 Address Types
IP Loopback Address
127.0.0.1 is the loopback address in IP. Loopback is a test mechanism of network adapters. Messages sent to 127.0.0.1 do not get delivered to the network. Instead, the adapter intercepts all loopback messages and returns them to the sending application. IP applications often use this feature to test the behavior of their network interface.
As with broadcast, IP officially reserves the entire range from 127.0.0.0 through 127.255.255.255 for loopback purposes. Nodes should not use this range on the Internet, and it should not be considered part of the normal Class A range.
Zero Addresses
As with the loopback range, the address range from 0.0.0.0 through 0.255.255.255 should not be considered part of the normal Class A range. 0.x.x.x addresses serve no particular function in IP, but nodes attempting to use them will be unable to communicate properly on the Internet.
Private Addresses
The IP standard defines specific address ranges within Class A, Class B, and Class C reserved for use by private networks (intranets). The table below lists these reserved ranges of the IP address space.
Nodes are effectively free to use addresses in the private ranges if they are not connected to the Internet, or if they reside behind firewalls or other gateways that use Network Address Translation (NAT).
IPv6 Address Types
IPv6 does not use classes. IPv6 supports the following three IP address types:
• unicast
• multicast
• anycast
Unicast and multicast messaging in IPv6 are conceptually the same as in IPv4. IPv6 does not support broadcast, but its multicast mechanism accomplishes essentially the same effect. Multicast addresses in IPv6 start with 'FF' (255) just like IPv4 addresses.
Anycast in IPv6 is a variation on multicast. Whereas multicast delivers messages to all nodes in the multicast group, anycast delivers messages to any one node in the multicast group. Anycast is an advanced networking concept designed to support the failover and load balancing needs of applications.
IPv6 Reserved Addresses
IPv6 reserves just two special addresses: 0:0:0:0:0:0:0:0 and 0:0:0:0:0:0:0:1. IPv6 uses 0:0:0:0:0:0:0:0 internal to the protocol implementation, so nodes cannot use it for their own communication purposes. IPv6 uses 0:0:0:0:0:0:0:1 as its loopback address, equivalent to 127.0.0.1 in IPv4.
source :http://compnetworking.about.com
Internet Protocol Tutorial Classes of IP Addresses, IP Broadcast and IP Multicast
IPv4 Address Classes
The IPv4 address space can be subdivided into 5 classes - Class A, B, C, D and E. Each class consists of a contiguous subset of the overall IPv4 address range.
With a few special exceptions explained further below, the values of the leftmost four bits of an IPv4 address determine its class as follows:
All Class C addresses, for example, have the leftmost three bits set to '110', but each of the remaining 29 bits may be set to either '0' or '1' independently (as represented by an x in these bit positions):
110xxxxx xxxxxxxx xxxxxxxx xxxxxxxx
Converting the above to dotted decimal notation, it follows that all Class C addresses fall in the range from 192.0.0.0 through 223.255.255.255.
IP Address Class E and Limited Broadcast
The IPv4 networking standard defines Class E addresses as reserved, meaning that they should not be used on IP networks. Some research organizations use Class E addresses for experimental purposes. However, nodes that try to use these addresses on the Internet will be unable to communicate properly.
A special type of IP address is the limited broadcast address 255.255.255.255. A broadcast involves delivering a message from one sender to many recipients. Senders direct an IP broadcast to 255.255.255.255 to indicate all other nodes on the local network (LAN) should pick up that message. This broadcast is 'limited' in that it does not reach every node on the Internet, only nodes on the LAN.
Technically, IP reserves the entire range of addresses from 255.0.0.0 through 255.255.255.255 for broadcast, and this range should not be considered part of the normal Class E range.
IP Address Class D and Multicast
The IPv4 networking standard defines Class D addresses as reserved for multicast. Multicast is a mechanism for defining groups of nodes and sending IP messages to that group rather than to every node on the LAN (broadcast) or just one other node (unicast).
Multicast is mainly used on research networks. As with Class E, Class D addresses should not be used by ordinary nodes on the Internet.
IP Address Class A, Class B, and Class C
Class A, Class B, and Class C are the three classes of addresses used on IP networks in common practice, with three exceptions as explained next.
source :http://compnetworking.about.com
Internet Protocol Tutorial
IP Address Notation - What Is An IP Address?
This tutorial explains the technology behind Internet Protocol (IP) networking. For those not interested in the technical aspects, skip to the following:
IPv4 and IPv6
Internet Protocol (IP) technology was developed in the 1970s to support some of the first research computer networks. Today, IP has become a worldwide standard for home and business networking as well. Our network routers, Web browsers, email programs, instant messaging software - all rely on IP or other network protocols layered on top of IP.
Two versions of IP technology exist today. Essentially all home computer networks use IP version 4 (IPv4), but an increasing number of educational and research institutions have adopted the next generation IP version 6 (IPv6).
IPv4 Addressing Notation
An IPv4 address consists of four bytes (32 bits). These bytes are also known as octets.
For readability purposes, humans typically work with IP addresses in a notation called dotted decimal. This notation places periods between each of the four numbers (octets) that comprise an IP address. For example, an IP address that computers see as
00001010 00000000 00000000 00000001
is written in dotted decimal as
10.0.0.1
Because each byte contains 8 bits, each octet in an IP address ranges in value from a minimum of 0 to a maximum of 255. Therefore, the full range of IP addresses is from 0.0.0.0 through 255.255.255.255. That represents a total of 4,294,967,296 possible IP addreses.
IPv6 Addressing Notation
IP addresses change significantly with IPv6. IPv6 addresses are 16 bytes (128 bits) long rather than four bytes (32 bits). This larger size means that IPv6 supports more than
300,000,000,000,000,000,000,000,000,000,000,000,000
possible addresses! In the coming years, as an increasing number of cell phones, PDAs, and other consumer electronics expand their networking capability, the smaller IPv4 address space will likely run out and IPv6 address become necessary.
IPv6 addresses are generally written in the following form:
hhhh:hhhh:hhhh:hhhh:hhhh:hhhh:hhhh:hhhh
In this full notation, pairs of IPv6 bytes are separated by a colon and each byte in turns is represented as a pair of hexadecimal numbers, like in the following example:
E3D7:0000:0000:0000:51F4:9BC8:C0A8:6420
As shown above, IPv6 addresses commonly contain many bytes with a zero value.Shorthand notation in IPv6 removes these values from the text representation (though the bytes are still present in the actual network address) as follows:
E3D7::51F4:9BC8:C0A8:6420
Finally, many IPv6 addresses are extensions of IPv4 addresses. In these cases, the rightmost four bytes of an IPv6 address (the rightmost two byte pairs) may be rewritten in the IPv4 notation. Converting the above example to mixed notation yields
E3D7::51F4:9BC8:192.168.100.32
IPv6 addresses may be written in any of the full, shorthand or mixed notation illustrated above.
source :http://compnetworking.about.com
CIDR - Classless Inter-Domain Routing
CIDR stands for Classless Inter-Domain Routing. CIDR was developed in the 1990s as a standard scheme for routing network traffic across the Internet.
Why Use CIDR?
Before CIDR technology was developed, Internet routers managed network traffic based on the class of IP addresses. In this system, the value of an IP address determines its subnetwork for the purposes of routing.
CIDR is an alternative to traditional IP subnetting that organizes IP addresses into subnetworks independent of the value of the addresses themselves. CIDR is also known as supernetting as it effectively allows multiple subnets to be grouped together for network routing.
CIDR Notation
CIDR specifies an IP address range using a combination of an IP address and its associated network mask. CIDR notation uses the following format -
xxx.xxx.xxx.xxx/n
where n is the number of (leftmost) '1' bits in the mask. For example,
192.168.12.0/23
applies the network mask 255.255.254.0 to the 192.168 network, starting at 192.168.12.0. This notation represents the address range 192.168.12.0 - 192.168.13.255. Compared to traditional class-based networking, 192.168.12.0/23 represents an aggregation of the two Class C subnets 192.168.12.0 and 192.168.13.0 each having a subnet mask of 255.255.255.0. In other words,
192.168.12.0/23 = 192.168.12.0/24 + 192.168.13.0/24
Additionally, CIDR supports Internet address allocation and message routing independent of the traditional class of a given IP address range. For example,
10.4.12.0/22
represents the address range 10.4.12.0 - 10.4.15.255 (network mask 255.255.252.0). This allocates the equivalent of four Class C networks within the much larger Class A space.
You will sometimes see CIDR notation used even for non-CIDR networks. In non-CIDR IP subnetting, however, the value of n is restricted to either 8 (Class A), 16 (Class B) or 24 (Class C). Examples:
• 10.0.0.0/8
• 172.16.0.0/16
• 192.168.3.0/24
How CIDR Works
CIDR implementations require certain support be embedded within the network routing protocols. When first implemented on the Internet, the core routing protocols like BGP (Border Gateway Protocol) and OSPF (Open Shortest Path First) were updated to support CIDR. Obsolete or less popular routing protocols may not support CIDR.
CIDR aggregation requires the network segments involved to be contiguous (numerically adjacent) in the address space. CIDR cannot, for example, aggregate 192.168.12.0 and 192.168.15.0 into a single route unless the intermediate .13 and .14 address ranges are included (i.e., the 192.168.12/22 network).
Internet WAN or backbone routers (those that manage traffic between Internet Service Providers) all generally support CIDR to achieve the goal of conserving IP address space. Mainstream consumer routers often do not support CIDR, therefore private networks (including home networks) and even small public networks (LANs) often do not employ it.
source : http://compnetworking.about.com
IP Variable Length Subnet Masking (VLSM)
Conventional Subnet masking replaces the two-level IP addressing scheme with a more flexible three-level method. Since it lets network administrators assign IP addresses to hosts based on how they are connected in physical networks, subnetting is a real breakthrough for those maintaining large IP networks. It has its own weaknesses though, and still has room for improvement. The main weakness of conventional subnetting is in fact that the subnet ID represents only one additional hierarchical level in how IP addresses are interpreted and used for routing.
The Problem With Single-Level Subnetting
It may seem “greedy” to look at subnetting and say “what, only one additional level”? However, in large networks, the need to divide our entire network into only one level of subnetworks doesn't represent the best use of our IP address block. Furthermore, we have already seen that since the subnet ID is the same length throughout the network, we can have problems if we have subnetworks with very different numbers of hosts on them—the subnet ID must be chosen based on whichever subnet has the greatest number of hosts, even if most of subnets have far fewer. This is inefficient even in small networks, and can result in the need to use extra addressing blocks while wasting many of the addresses in each block.
For example, consider a relatively small company with a Class C network, 201.45.222.0/24. They have six subnetworks in their network. The first four subnets (S1, S2, S3 and S4) are relatively small, containing only 10 hosts each. However, one of them (S5) is for their production floor and has 50 hosts, and the last (S6) is their development and engineering group, which has 100 hosts.
The total number of hosts needed is thus 196. Without subnetting, we have enough hosts in our Class C network to handle them all. However, when we try to subnet, we have a big problem. In order to have six subnets we need to use 3 bits for the subnet ID. This leaves only 5 bits for the host ID, which means every subnet has the identical capacity of 30 hosts, as shown in Figure 70. This is enough for the smaller subnets but not enough for the larger ones. The only solution with conventional subnetting, other than shuffling the physical subnets, is to get another Class C block for the two big subnets and use the original for the four small ones. But this is expensive, and means wasting hundreds of IP addresses!
Figure 70: Class C (/24) Network Split Into Eight Conventional Subnets
With traditional subnetting, all subnets must be the same size, which creates problems when there are some subnets that are much larger than others. Contrast to Figure 71
The Solution: Variable Length Subnet Masking
The solution to this situation is an enhancement to the basic subnet addressing scheme called Variable Length Subnet Masking (VLSM). VLSM seems complicated at first, but is easy to comprehend if you understand basic subnetting. The idea is that you subnet the network, and then subnet the subnets just the way you originally subnetted the network. In fact, you can do this multiple times, creating subnets of subnets of subnets, as many times as you need (subject to how many bits you have in the host ID of your address block). It is possible to choose to apply this multiple-level splitting to only some of the subnets, allowing you to selectively cut the "IP address pie" so that some of the slices are bigger than others. This means that our example company could create six subnets to match the needs of its networks, as shown in Figure 71.
Figure 71: Class C (/24) Network Split Using Variable Length Subnet Masking (VLSM)
Using VLSM, an organization can divide its IP network multiple times, to create subnets that much better match the size requirements of its physical networks. Contrast to Figure 70.
An Example: Multiple-Level Subnetting Using VLSM
VLSM subnetting is done the same way as regular subnetting; it is just more complex because of the extra levels of subnetting hierarchy. You do an initial subnetting of the network into large subnets, and then further break down one or more of the subnets as required. You add bits to the subnet mask for each of the "sub-subnets" and "sub-sub-subnets" to reflect their smaller size. In VLSM, the slash notation of classless addressing is commonly used instead of binary subnet masks—VLSM is very much like CIDR in how it works—so that's what I will use.
Note: Before proceeding to the VLSM example that follows, a suggestion: if you aren't feeling comfortable with how basic subnetting works, you probably want to read through the section on practical subnetting first. Trust me. :)
Let's take our example above again and see how we can make everything fit using VLSM. We start with our Class C network, 201.45.222.0/24. We then do three subnettings as follows (see Figure 72 for an illustration of the process):
1. We first do an initial subnetting by using one bit for the subnet ID, leaving us 7 bits for the host ID. This gives us two subnets: 201.45.222.0/25 and 201.45.222.128/25. Each of these can have a maximum of 126 hosts. We set aside the first of these for subnet S6 and its 100 hosts.
2. We take the second subnet, 201.45.222.128/25, and subnet it further into two sub-subnets. We do this by taking one bit from the 7 bits left in the host ID. This gives us the sub-subnets 201.45.222.128/26 and 201.45.222.192/26, each of which can have 62 hosts. We set aside the first of these for subnet S5 and its 50 hosts.
3. We take the second sub-subnet, 201.45.222.192/26, and subnet it further into four sub-sub-subnets. We take 2 bits from the 6 that are left in the host ID. This gives us four sub-sub-subnets that each can have a maximum of 14 hosts. These are used for S1, S2, S3 and S4.
4. 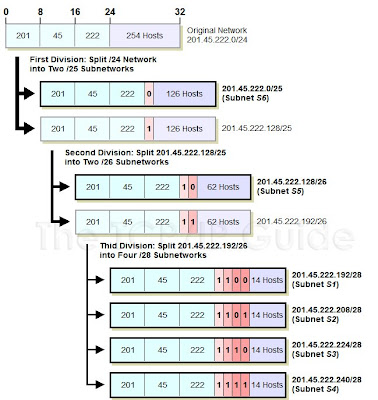
Figure 72: Variable Length Subnet Masking (VLSM) Example
This diagram illustrates the example described in the text, of a Class C (/24) network divided using three hierarchical levels. It is first divided into two subnets; one subnet is divided into two sub-subnets; and one sub-subnet is divided into four sub-sub-subnets. The resulting six subnets are shown with thick black borders, and have a maximum capacity of 126, 62, 14, 14, 14 and 14 hosts.
Okay, I did get to pick the numbers in this example so that they work out just perfectly, but you get the picture. VLSM greatly improves both the flexibility and the efficiency of subnetting. In order to use it, routers that support VLSM-capable routing protocols must be employed. VLSM also requires more care in how routing tables are constructed to ensure that there is no ambiguity in how to interpret an address in the network.
As I said before, VLSM is similar in concept to the way classless addressing and routing (CIDR) is performed. The difference between VLSM and CIDR is primarily one of focus. VLSM deals with subnets of a single network in a private organization. CIDR takes the concept we just saw in VLSM to the Internet as a whole, by changing how organizational networks are allocated by replacing the single-level “classful” hierarchy with a multiple-layer hierarchy.
source :www.tcpipguide.com/

